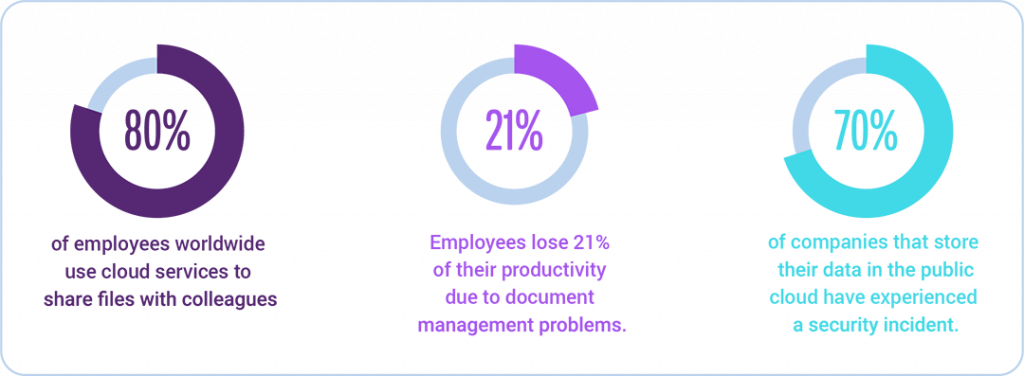
Why is Unified Endpoint Management (UEM) essential for your business's success?
To configure and manage all your mobile devices with one comprehensive and effective software is integral to the security and productivity of your business. We offer simple strategies for complex processes.

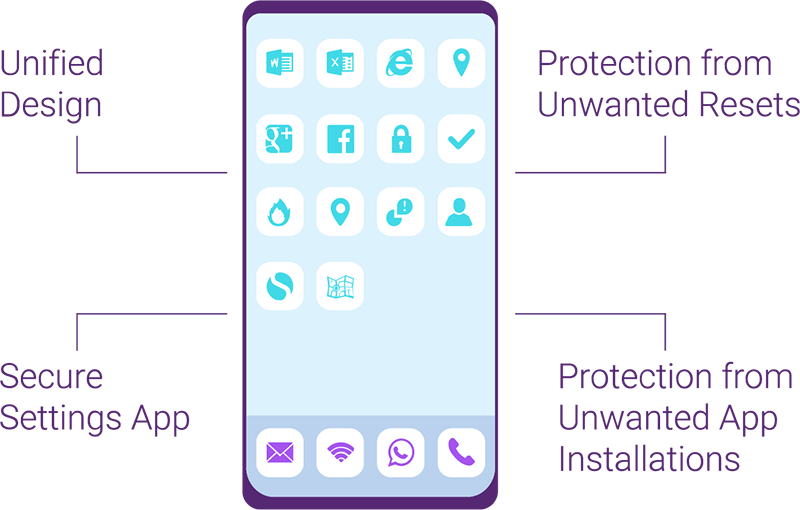
Reliable Protection For Corporate Data
With our UEM Secure Connection & Identity Package, you can always safeguard your worker’s mobile data traffic - or that of your customers and partners - and govern mobile apps and devices.

Our services are tailored to your individual needs
To provide the best possible result and optimal usability we offer maintenance, adaptation to changing conditions and further development to tailor our product to your specific needs. Perfect functionality, flexibility, and modern architecture as decisive competitive factors for companies are our priorities.

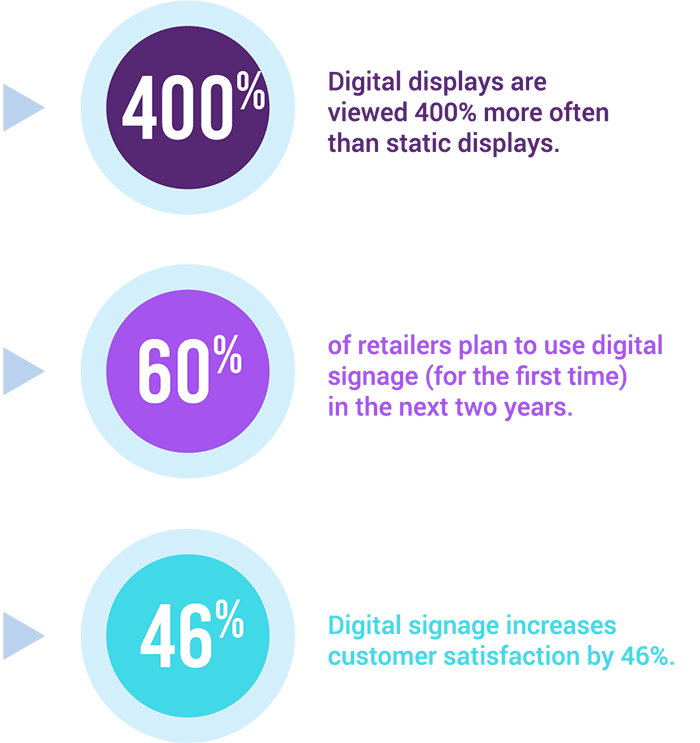
Synchronize, Share, and Host Mobile Content Yourself
Our Enterprise Mobility Management can not only manage your in-house devices but is also equipped to allow for Bring Your Own Device (BYOD) solutions. BYOD allows employees to use their own mobile devices to access your firmware and data. This has proven to not only increase employee satisfaction and productivity but also to reduce costs.
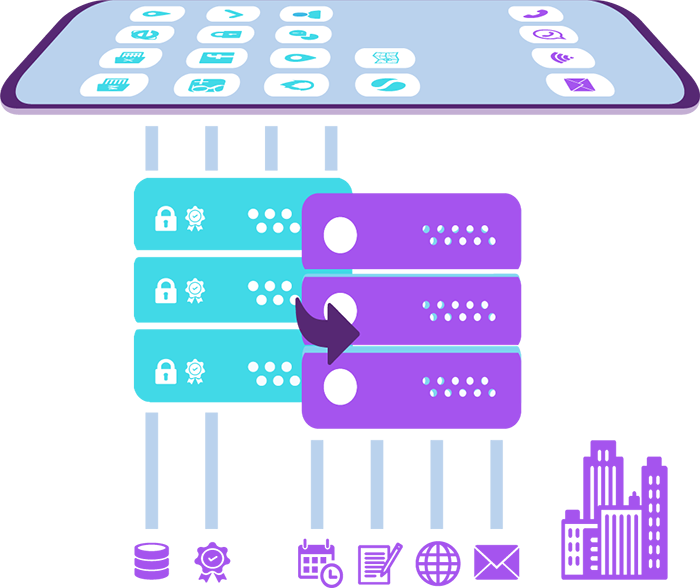
Remote Working Made Simple and Secure
Unified Endpoint Management is a vital necessity.we offers you efficient and high-grade UEM Software Solutions that allow you to manage and configure all your mobile devices easily and safely.
Our Enterprise Mobile Manage is a tried-and-true technique and toolkit for providing mobile productivity tools and applications to employees while keeping corporate data safe. It is the management of mobile devices such as cellphones, tablet computers, and laptop computers.
Services and Perks offered
- Management console accessible over the internet.
- Architecture that can support several clients.
- Integration with LDAP.
- Portal for self-service.
- User-friendly administration dashboard, you can control all devices in the organization on any computer at any time.
- From a single installation, you can effortlessly manage several clients with different domains.
- Tamper-resistant logging guarantees that the settings and administrative procedures may be replicated.
What are you waiting for?

Give us a call or drop by anytime, we endeavour to answer all inquiries
within 24 hours on business days. We will be happy to answer your questions.
Copyrights All rights reserved by Looptech - Our Privacy Policy



