
A Deceivingly Simple Solution to Complex Threats
Deception Platform changes an attack surface providing adversaries with an illusion of real infrastructure vulnerabilities.
Each part of the imitated environment reproduces the services and content of a real network segment.
Utilizing high-interaction decoys and lures, deception deceives attackers into revealing themselves, thereby alerting on and identifying detection gaps on threats that have evaded other security controls.
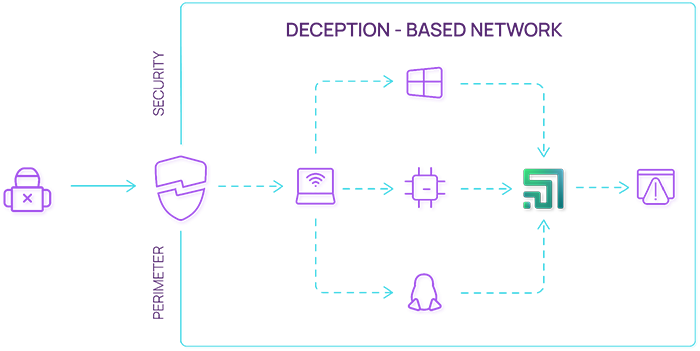
Deception Platform - This is how it works
Points mimic special software services, content, routers, devices etc. Each Point detects all targeted suspicious activities.
While the attacker proceeds through the fake aim infrastructure, Deception platform captures all the hostile’s details.
The company receives information about threat sources, the tools that were used, and about exploited vulnerabilities and the attacker’s behavior.
In the meantime, the whole real infrastructure continues to work without any impact.
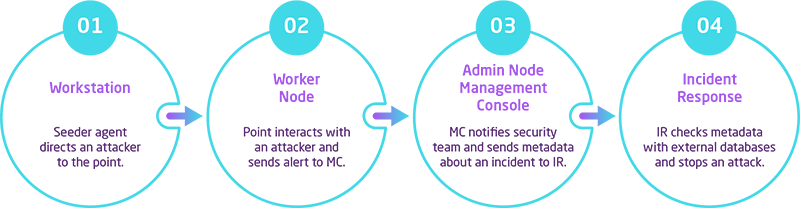
LABYRINTH Deception Technology
Targeted Attacks Uncovering

Post-Infection Detection

Lateral Movement Recognition

Dwell Time Reduction

Early In-Network Threat Detection

Accurate Alerts

Rapid Incident Response

Proactive Defense
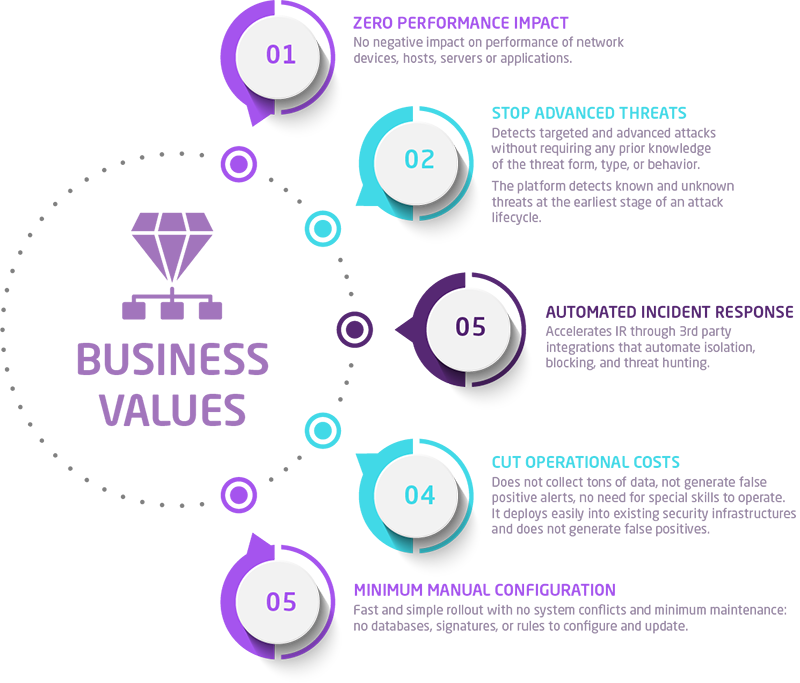
Key Benefits
Deception Platform provides the most efficient tool to detect and stop hackers’ movements inside the corporate network.
- Accurate and early in-network threat detection for any threat vector.
- Comprehensive solution with scalability for evolving attack surfaces.
- Easy deployment, operation, and scalability.
- Ability to win additional time on incident response while attacker is in Labyrinth.
- Detailed attack information, including attack tactics and tools.
- Highly reliable alerts with less than 1% false positives.
- Less data for analysis and less digital “noise” production.
What are you waiting for?

Give us a call or drop by anytime, we endeavour to answer all inquiries
within 24 hours on business days. We will be happy to answer your questions.
Copyrights All rights reserved by Looptech - Our Privacy Policy



